Non-secure deltas
The competition and its Non-Secure DELTA files
As specified in the previous slides,
We will give an example on how SecureDELTA creates secured binary diff files and how the competition, here, Leading Competitor software creates non secured binary diff files
Here is a SCENARIO:
A SECRET KEY is appended in the end of the TARGET FILE. The SOURCE file will be ‘patched’ with a delta file containing a SECRET KEY which SHOULD NOT be visible during the update.
Here is the target file content with the SECRET KEY appended in the end. The SECRET KEY is marked with a red square:
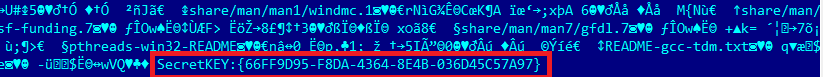
After creating the Leading Competitor binary diff file it is noticeable that it contains the SECRET KEY in the clear, see below:
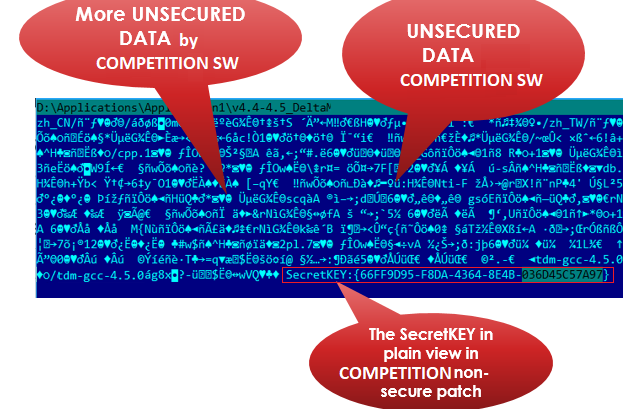
Also, other pieces of information are visible, for instance file paths or any other binary information.
Leading Competitor binary diff files may leave most of the information in the clear, exactly as it appears in the TARGET file.
Leading Competitor binary diff files may contain unsecured data from the target file in plain text when such data needs to be copied from the target file.
Choose SecureDELTA to protect your data!
Given the unknown method of securing a transport channel for the binary diff file: if you use a Leading Competitor software and your diff files are sent over a non-secure channel, you are simply sending your binary diff file with a plain, in sight, Secret KEY over the (internet) network.